#Product Trends
The importance of time synchronization in IT security
More and more data requires new solutions
Increasing digitization is a major challenge for the economy. Constantly increasing amounts of data have to be transferred, and there is always the danger of unauthorized access, manipulation or industrial espionage. Where large companies can afford specialists for this field, especially in small and medium-sized enterprises there is a lack of expertise and competence. Industry associations, politics and the protection of the constitution have been warning for a long time.
The Federal Office for Information Security (BSI) offers technical support and publications in various areas, such as the brochures "IT Security Law", "Critical Infrastructure Protection - Risk and Crisis Management". A Guide for Enterprises and Authorities "or" Critical Infrastructure Protection: Risk Management in the Hospital "of the Federal Office for Civil Protection and Disaster Assistance.
The BSI "Guide to IT Forensics" also provides companies and authorities with valuable information on what should be considered from the outset in the architecture of IT systems in the case of "IT Security by Design". IT forensics is a sub-discipline of security, as malfunctions or malfunctions of an IT infrastructure can be detected, analyzed and remedied.
Some medium-sized companies are also already dealing with topics such as IT emergency management in practice. For example, J. Schmalz GmbH from Glatten, which was awarded the Security Prize of the State of Baden-Württemberg for its IT security concept in 2015, can certainly be exemplary for other SMEs in Germany.
How great the danger is, many are unaware. In the process, attacks via the Internet can not only paralyze entire production processes, but can become a major risk to the entire population, especially among energy suppliers or power plant operators. Also a reason why the protection of the constitution has adopted the subject and in 1999 the "Security Forum Baden-Württemberg - The economy protects their knowledge" has launched. This is an independent body of companies, associations, research institutes, chambers and authorities. This safety forum aims to protect the technology advantage of Baden-Württemberg's economy and research against industrial espionage. The aim is to better recognize dangers and protect companies, especially small and medium-sized businesses.
Because the digitization of the economy and all social levels is continuing inexorably. For example, the implementation of "smart energy" coupled with decentralization of power generation in conjunction with more and more intelligent "Internet of Things" devices is leading to a variety of control and terminal devices in the emerging networks complex IT attacks. Among other things, the public utility companies, such as the elementally important gas-, water- and electricity- suppliers, are sensitive building blocks of a functioning infrastructure and therefore particularly worthy of protection.
The term "smart environment" also includes developments in the hospital sector, where, in addition to the digitization, personal medical records, surveillance systems for video-based fall monitoring are currently being introduced, for example. Again, the necessary databases and data centers pose new challenges for IT security standards.
In the case of manufacturing companies in particular, intensive work is currently being done on Industry 4.0, also the pervasive networking of all value-added chains. As a result of the collection and evaluation of an unprecedented wealth of digital data, a drastically increased production flexibility up to the "one-piece lot size" and the anchoring of these processes in suitable hardware and software systems, the protection of these IT systems is likely to gain in the future an outstanding importance for the business continuity of these companies.
These are just a few examples of how digital life will affect our future lives and where serious potential threats could affect our businesses and the economy as a whole. So it is now a recognized acknowledgment among experts that the wars of the future will increasingly play out in cyber-space and that Germany is already targeted in the sights of, for example, Russian and Chinese organizations. Even government agencies have already responded to this and set up new, special departments for cyber crime in the federal and state criminal police departments, which, among other things, focus on cyber investigations, IT evidence preservation and telecommunications surveillance increasing trend. Even large corporations have already set up specialist departments for IT damage prevention, but it is precisely for Germany very important and traditionally technology-oriented SMEs that are often not aware of these dangers.
Meaning of time synchronization
In the "Catalog of Measures Hard- and Software - IT Grundschutz Catalogue, M.4227 Use of a Local NTP Server for Time Synchronization", the BSI points to the importance of precise time synchronization. It is thus "important in networked systems that all affected computers have a correct system time". In addition, it is also stated in this publication that, especially in the evaluation of logging information, for example of error messages or in applications distributed over several computers, the correct time synchronicity has an elementary significance.
It is probably also obvious to the IT practitioner in the context of "Industry 4.0" that every database entry can only be fully used if the respective time stamp can be unambiguously and correctly assigned to this protocol. Frequently, however, in current business practice, external time sources such as the Internet-accessible NTP time server of the Physikalisch-Technische Bundesanstalt (PTB) in Braunschweig are still used today. However, in the sense of an IT strategic security architecture, any physical access to the outside world should be avoided. For example, a cybercrime offense can also be that unusual processes are running on the system, which take up large amounts of data resources.
The German Federal Office of Criminal Investigation (BKA) also points out this. The BSI also comes in the above-mentioned catalog of measures therefore rather to the conviction that "alternatively local time servers are used" and "in case of doubt (then) this solution is preferable" to give.
Recommendations for time server solutions
Here again reference can be made to the "Guidelines for IT Forensics" of the BSI. On page 38ff. In detail, the "meaning of time" is explained and partial aspects such as time sources, timestamps or the assurance of a reliable time source are pointed out in detail.
With regard to the strategic preparation - also in terms of the system architecture and the necessary IT investments - it is demonstrated in particular in the latter case that ultimately there are three expansion stages to ensure the correct system time. The low should allow at least synchronization of the computer network using the Network Time Protocol (NTP), with external sources still the fundamental danger of disturbing incidents or deliberate attacks. The medium expansion stage means that the system operator can integrate an additional receiving device in the form of a DCF receiver into his computer network, whereby this receiver then converts the radio signals into an internally usable NTP packet. However, these radio signals and data packets generated therefrom are then not completely protected against deliberate manipulation. For those who want to be on the safe side, the BSI recommends a combination of DCF and GPS receivers, whereby the timing devices should also contain a high-quality, internal time source. Thus, it is then possible to detect any time differences between the two external sources and to warn the system operator accordingly or at least initiate the necessary countermeasures in good time.
High quality time servers from MOBATIME
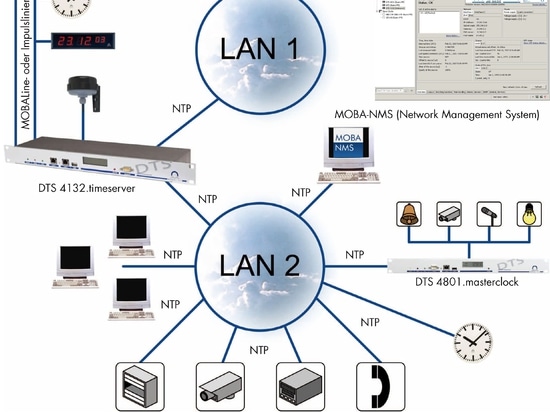
The company Bürk Mobatime from Schwenningen has been offering high-quality NTP time servers for ten years, which are used in a wide range of applications. Particularly in the area of critical infrastructures, a solution has proved itself over the years which clearly corresponds to the high expansion stage of the BSI recommendation.
The relevant plant operators - for example, at the automation level of power plants worldwide - often opt for a time system architecture, which consists of two redundant NTP time servers, each with a GPS receiver. The GPS receivers refer not only to one, but several satellites and are thus configured very fail-safe in this respect. However, even if these external GPS radio time sources should fail, each time server again has its own, high-quality and usually quartz-based internal timekeeping. Independently of the other, both time servers are then always connected to the IT network and permanently stored as the first or second time source in the network devices. The two time servers - regardless of the network - are still in direct contact with each other and always set identical time temps by means of appropriate synchronization and intelligent software trimming. As a result, any time jumps that would otherwise be critical throughout the IT systems can be avoided when switching over.
Even data centers in university or other utilities networks, such as municipal utilities, increasingly use this type of IT time system architecture and can fall back on various time server products in our range of services. Depending on the desired price-performance ratio, the products offered differ, among other things, in the number of LAN ports, in the form of other, possibly additionally required time interfaces or also by the quality of the internal time base and "holdover accuracy". , For a corresponding product consultation or further information on the subject of "IT security" the professionals of Bürk Mobatime are at your disposal.
Author: Stephan Herrmann, Managing Director
Links and References:
https://www.bsi.bund.de
http://www.sicher-im-netz.de
http://bitkom.org
http://bmwi.de
http://asw-online.de
http://www.bka.de
http://www.sicherheitsforum-bw.de/pb/,Lde/Startseite/Das+Sicherheitsforum+Baden_Wuerttemberg/Sicherheitspreis+2015
„Maßnahmenkatalog Hard- und Software – IT Grundschutz-Kataloge“ des Bundesamtes für Sicherheit in der Informationstechnik, 53133 Bonn.
„Leitfaden IT-Forensik“ des Bundesamtes für Sicherheit in der Informationstechnik, 53133 Bonn.
Brochure „Cybercrime – Handlungsempfehlungen für die Wirtschaft in Fällen von Cybercrime“ des Bundeskriminalamtes, Referat SO41, 65173 Wiesbaden.